When you want to scan images within Datacap Navigator you will need to install the Dynamsoft TWIN driver provided by IBM Datacap. After the installion you might be not able to select a scanner within the scan task. This could happen because of a wrong configured ESAPIWafPolicy of you IBM Content Navigator deployment.
Check the ESAPIWafPolicy.xml used by the Content Navigator deployment and change it with the required parameters.
The location of the ESAPIWafPolicy.xml you will find in the web.xml of the navigator deployment. By default this is located under <WAS_HOME>\profiles\<profileName>\installedApps\<NodeName>\navigator.ear\navigator.war\WEB-INF\web.xml
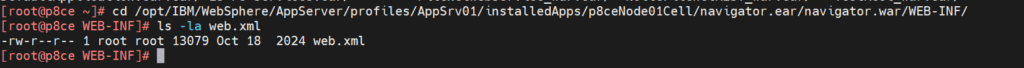
Open the web.xml and search for „ESAPIWafPolicy“.
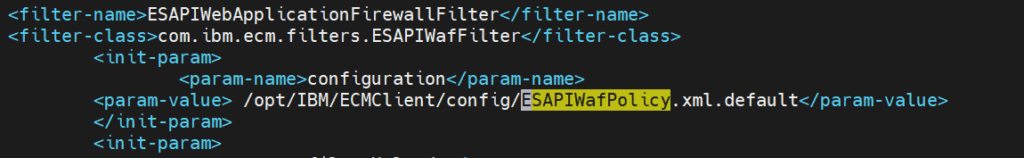
By default the file is located under \ECMClient\config.
Now open ESAPIWafPolicy.xml in an editor and replace the content with the following:
<?xml version="1.0" encoding="UTF-8"?>
<policy>
<aliases/>
<settings>
<mode>block</mode>
<error-handling>
<default-redirect-page>/error.jsp</default-redirect-page>
<block-status>500</block-status>
</error-handling>
</settings>
<virtual-patches>
<!-- Uncomment and update to add return host validation when enableOAuthProxy is set to true in web.xml
<virtual-patch id="oauth2-return" path=".*/jaxrs/oauth2/.*"
variable="request.parameters.state"
pattern="^(localhost|localhost:http)$"
message="Detected invalid OAuth2 return host.">
</virtual-patch>
-->
</virtual-patches>
<outbound-rules>
<add-header name="Cache-Control" value="no-cache, no-store" path=".*/|.*\.jsp|.*/jaxrs/.*|.*/api/.*"/>
<add-header name="Content-Security-Policy" value="default-src 'self' blob: https:; connect-src 'self' blob: https: http://127.0.0.1:* https://127.0.0.1:* ws://127.0.0.1:* wss://127.0.0.1:*;
font-src 'self' data: blob: https:; img-src 'self' data: blob: https:; script-src 'self' 'unsafe-inline' 'unsafe-eval' https:; worker-src 'self' blob: https:; style-src 'self' 'unsafe-inline' https:; frame-ancestors 'self'" path="/.*"/>
<!-- <add-header name="Content-Security-Policy"
value="default-src 'self' blob: https:; font-src 'self' data: blob: https:; img-src 'self' data: blob: https:; script-src 'self' 'unsafe-inline' 'unsafe-eval' https:; worker-src 'self' blob: https:; style-src 'self' 'unsafe-inline' https:; frame-ancestors 'self'"
path="/.*"/> -->
<add-header name="Referrer-Policy" value="same-origin" path="/.*"/>
<add-header name="Strict-Transport-Security" value="max-age=7776000; includeSubdomains" path="/.*"/>
<add-header name="X-Content-Type-Options" value="nosniff" path="/.*"/>
<add-header name="X-Frame-Options" value="sameorigin" path="/.*"/>
<add-header name="X-Permitted-Cross-Domain-Policies" value="none" path="/.*"/>
<add-header name="X-XSS-Protection" value="1; mode=block" path="/.*"/>
</outbound-rules>
<url-rules>
<!-- Deny HTTP methods other than GET, POST, PUT, DELETE, HEAD, and OPTIONS, and only allow POST for logon requests -->
<restrict-method deny="^((?!GET|POST|PUT|DELETE|HEAD|OPTIONS).)*$"/>
<restrict-method deny="^(GET|PUT|DELETE|HEAD|OPTIONS)$" path=".*/jaxrs(/|/.+/)logon$"/>
</url-rules>
</policy>Save the changes and restart the WebSphere server hosting the Content Navigator application. Now when you open the scan task you will be able to select you connected scanners.
